Roheed Khan

AI Headphones Breakthrough: Real-Time Multi-Speaker Translation with 3D Voice Cloning
A revolutionary development in AI technology has emerged with the unveiling of new headphones capable of translating multiple speakers in ...

Nintendo Revises User Agreement to Tackle Emulation and Piracy Concerns
Nintendo has updated its user agreement, taking a firmer stance against emulation, hacking, and piracy, with a warning that it ...

Google Gemini 2.5 Models Roll Out Implicit Caching for Cost Efficiency
Google has launched implicit caching for its Gemini 2.5 models, a feature that automatically applies a 75% token discount on ...

Google NotebookLM to Introduce Video Overviews for Simplified Note Summaries
Google is set to enhance its AI-powered note-taking tool, NotebookLM, with a new “Video Overviews” feature that creates short video ...

Apple Targets 2027 for Smart Glasses with Custom AR Chips
Apple is gearing up to launch smart glasses by 2027, featuring custom chips designed for augmented reality (AR) and low-power ...

Baidu’s AI Seeks to Decode Animal Sounds into Human Language
Baidu, a leading Chinese tech company, has filed a patent for an AI system that could translate animal vocalizations into ...
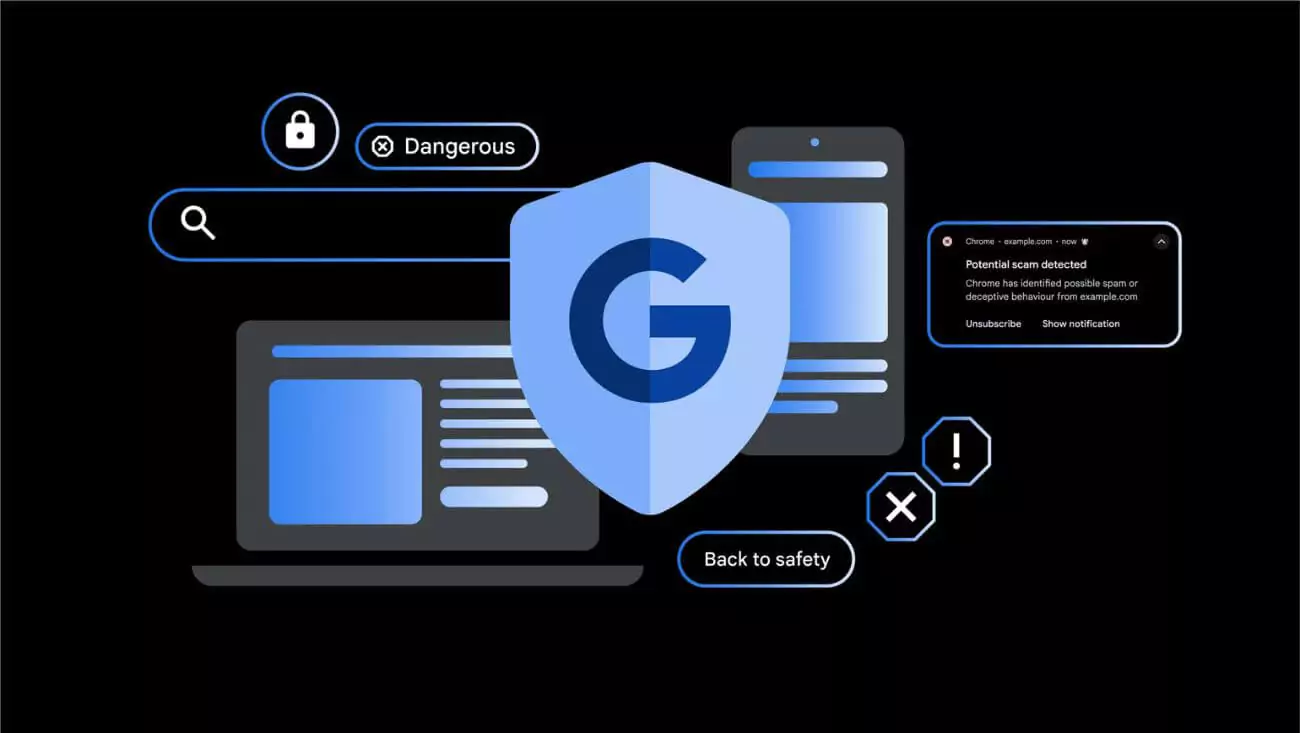
Google’s AI Scam Defense Tools Arrive for Chrome and Search Users
Google has launched a new set of AI-powered tools to protect users from online scams, enhancing security across Chrome and ...
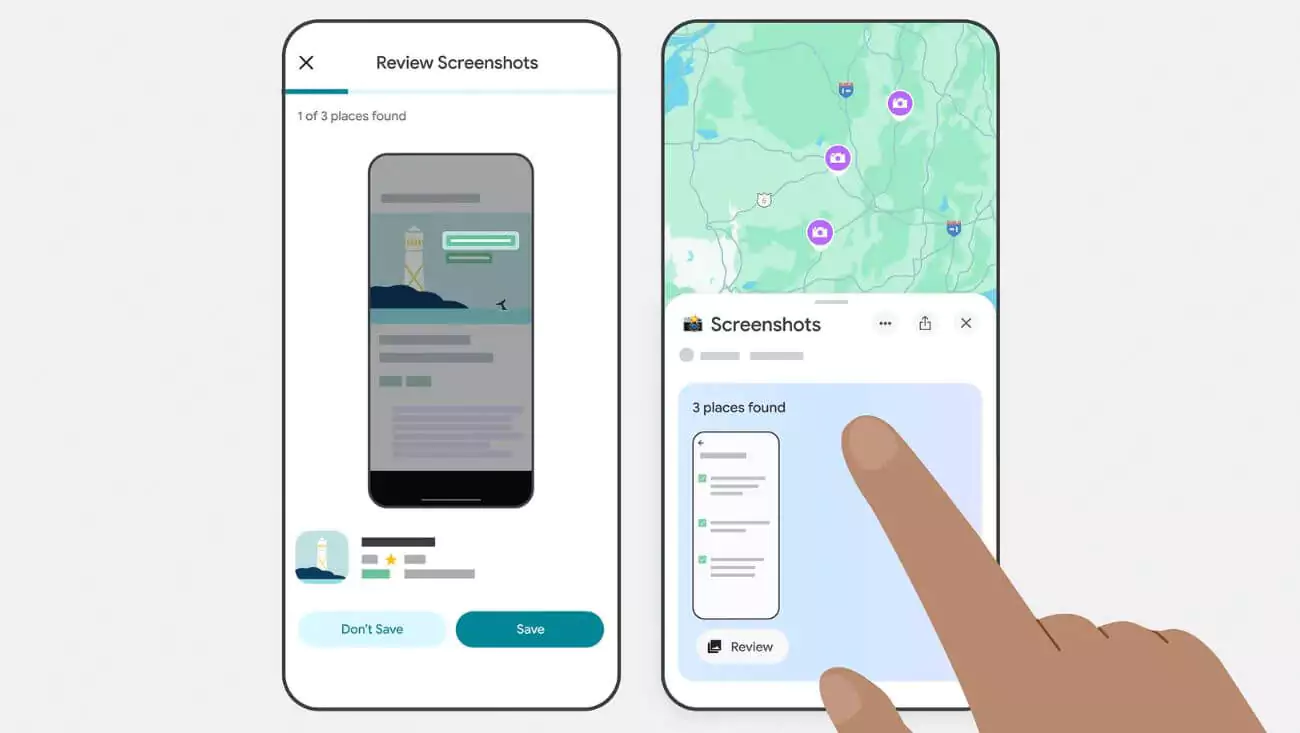
Google Maps’ New iPhone Feature Uses Gemini AI to Scan Screenshots
Google Maps has introduced a groundbreaking feature for iPhone users, utilizing Gemini AI to scan screenshots and save location data ...

New U.S. Bill Could Open iPhones to Third-Party App Stores
A recently introduced U.S. bill, the App Store Freedom Act, could require Apple to allow third-party app stores on iPhones, ...

Apple Settles $95M Siri Privacy Lawsuit: Here’s How to Claim Your Payout
Apple has secured final approval for a $95 million settlement to resolve a class action lawsuit claiming that its Siri ...