With more assets connected to the Internet, there is a greater risk of malicious attacks, unauthorized access, and data breaches, which can have serious consequences such as leakage of personal or sensitive data, manipulation or control of connected devices, or a business being shut down and held hostage. As a result, establishing robust security mechanisms and standards is critical to protecting the integrity and trustworthiness of IoT devices and ensuring a safer, more trustworthy digital environment.
While a hacker may not be interested in how warm your house is, a smart thermostat might be used as a doorway to obtain access to important data, such as personal information and private documents, which could then be sold on the dark web.
Risks and Consequences of Security Breaches
Security is an essential aspect of IoT device management. Understanding the possible risks and implications of security breaches in IoT is critical for enterprises seeking to secure their operations, preserve user privacy, and retain system confidence.
1. Exposure to Cyber Threats
As gadgets interact, cyber dangers become more prevalent. The danger range is broad, ranging from unauthorized access to data modification. Cybercriminals exploit weaknesses, possibly jeopardizing the integrity of data and functioning.
2. Service Disruption
A hacked IoT device may interrupt whole systems in addition to posing a data danger. Whether it’s a smart city infrastructure or an industrial process, security breaches may disrupt operations, resulting in financial losses and, in the worst-case scenario, putting public safety at risk.
3. Data Breach and Privacy Concerns
Security breaches frequently result in unauthorized access and data exposures. In an IoT environment where personal and sensitive information is traded, the ramifications of a data breach go beyond monetary losses. Privacy considerations become crucial, influencing user trust and confidence.
Challenges in Implementing IoT Security
Implementing IoT security can be challenging due to the complexity of securing diverse ecosystems.
- Diverse Device Landscape: The sheer number of IoT devices, from smart home gadgets to industrial sensors, presents a dilemma. Securing this heterogeneous environment necessitates adaptive solutions that address the specific security requirements of each device type.
- Interconnected Networks: The extensive web of interconnecting networks heightens the complexity. Ensuring a consistent degree of security across several communication protocols and platforms is a daunting challenge that necessitates a deliberate, all-encompassing strategy.
- Resource Limitations: Many IoT devices have limited processing power and storage capacity. Balancing comprehensive security measures with these resource limits is a difficult act to avoid jeopardizing device performance.
- Cost-Effective Solutions: Advanced security features frequently come with a cost. Striking a balance between strong security and cost-effectiveness is critical for encouraging wider use of safe IoT activities.
Best Practices for Securing IoT Devices
Securing IoT devices is crucial for preventing possible breaches and ensuring the integrity, confidentiality, and availability of data and operations. Here are some best practices for secure IoT device management.
- Securing Data: Implementing robust encryption techniques guarantees that data transmitted between devices and kept on them is secure. This protects against unauthorized access and data breaches.
- Regular Software Updates and Firmware Policies: Regular updates fix security flaws and improve device resilience. Establishing explicit firmware policies ensures that devices are up to current with the latest security updates.
- Securing Communication Channels: Firewalls serve as a barrier to unauthorized access, shielding IoT devices from external dangers. Intrusion detection systems actively monitor network activity, identifying and responding to possible security breaches.
- Strengthening the Device Identity: Robust device authentication guarantees that only authorized devices have access to the IoT network. This entails establishing safe authentication techniques and policies.
- Increasing Security Using Multi-Factor Authentication (MFA): Adding an extra layer of authentication using multi-factor methods like biometrics or one-time passwords greatly improves device security.
- Real-Time Monitoring and Anomaly Detection: It’s crucial to have monitoring systems that can detect anomalous activity in real time. Anomaly detection helps to discover possible security vulnerabilities quickly, allowing for fast mitigation steps.
- Prioritize Privacy by Design: When designing and developing Internet of Things (IoT) devices, privacy must be taken into account from the outset. To safeguard user privacy, data gathering should be limited to vital information and anonymized wherever feasible.
Key Threats to IoT Device Security
Understanding the many cyber dangers in the complex web of linked devices is critical to strengthening IoT security. Let’s look at the many issues that threaten the integrity of IoT ecosystems.
Denial-of-Service (DoS) Attacks
Cyber attackers flood IoT devices with traffic, preventing them from working. This interrupts services and, in serious cases, can result in system breakdowns.
Malicious Software
Malicious software infiltrates devices, causing them to malfunction or encrypt data until a ransom is paid. This provides a twofold hazard, affecting device performance and potentially resulting in data loss.
Man-in-the-Middle Attacks (MitM)
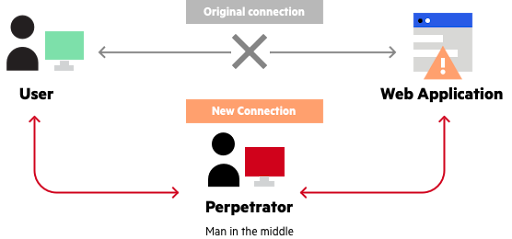
In a MitM attack, hackers intercept and modify data transmission between devices to obtain unauthorized access to confidential information. This form of assault is especially dangerous in networked systems.
Eavesdropping
Unsecured communication connections render IoT devices vulnerable to eavesdropping. Attackers can intercept and modify data, providing major privacy and security concerns.
Device Spoofing & Impersonation
By impersonating authorized devices, fraudsters can get unauthorized access. This opens the door to data manipulation, unauthorized control, and even system penetration.
Conclusion
As IoT devices become more prevalent in our lives, strong security measures are required to safeguard users and their data from potential cyber attacks. Manufacturers and consumers may help improve the security posture of IoT devices by following the procedures and measures mentioned below. Emphasizing security throughout the IoT lifespan will contribute to the creation of a connected society that is safe, secure, and robust to emerging cyber threats.