Compliance with security regulations is a never-ending process. As new features and developments are implemented, your company’s environment is constantly evolving. In the process of these dynamic evolutions, previously upheld regulatory constraints may be pressured or breached, which can cause problems during deployment. To ensure this non-compliance doesn’t occur, teams must undertake regular monitoring and reporting.
Managing Security Compliance
An organization’s database can contain a large amount of personal data on users, and it is vital to verify that the data is safe. If the attacker has access to the database, they will be able to see all of the personal information and manage the company.
There are various options for dealing with this circumstance; we must keep an eye on the goods and update them if any faults or mistakes are found. Another option is to employ intelligent automated technologies to discover the flaws and verify that the product is secure.
When building the software, we can utilize scripts or automated tools to discover flaws in the code. For example, you may use the script to check for code standards, SQL injection issues, and cross-site injection. We may find code problems when building software with the help of the script or SAST tools.
There are two methods for finding software vulnerabilities: white-box testing and black-box testing. White-box testing is carried out manually by inspecting the code of its infrastructure or through the automated static analysis approach, which may also be carried out manually. On the other hand, black-box testing is done after the development process since it is based on the software’s results and compares them to the predicted outcome.
We can address security problems by employing various white-box testing techniques, but the drawback is that we must repeat the process after each development step. Instead, we should use an automatic script or procedure that validates the code even after a minor update. We can then avoid problems like SQL injection, CSRF, etc.
It will be more expensive to identify software defects later than discover them early. Developers also must find flaws as quickly as possible. However, fewer experienced developers are available to do so, and the code structure is complex for a newbie developer to understand. As a result, discovering vulnerabilities while developing software is preferable, which we can achieve with SAST.
Mitigating Flaws
An organization or a user can prevent security problems by following the SDLC (Software Development Lifecycle). Many paradigms, such as agile, waterfall, and development and operations (DevOps), are part of SDLC to increase security. In addition, many firms nowadays employ the SDLC to mitigate security issues.
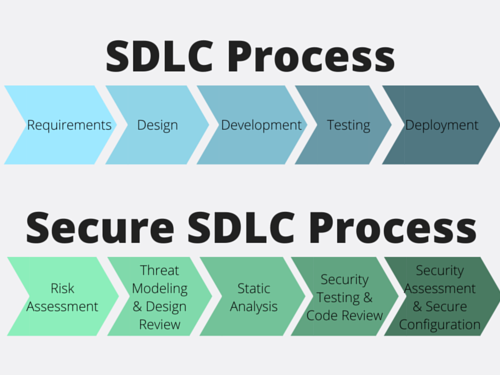
Even if the SDLC models are followed, there will still be some faults since they illustrate the lifecycle of following the development cycle in which many problems are avoided. Still, they are not the only approach to reduce flaws. Instead, we should use the SDLC models with a static analytical process. So, we can mitigate the issues by observing the lifecycle and the automated scripts that will run concurrently while building the product.
To address compliance issues within an SDLC model, there are three dominant areas you can focus on. The first is shifting security left – this basically means developers and testers can focus on security immediately without needing access to resources. It can help reduce the cycle from days to minutes and increase focus on functionality, quality, and security.
Next, build security directly into your policies so that the policy-driven infrastructure can automatically determine compliance for specific units and tools. Finally, create an audit trail so you can always maintain and prove compliance throughout your SDLC. Logging all activities using an automation tool will capture every little detail that pertains to your data and its transfer and presence from development to production.
Conclusion
There are several vulnerabilities out there, and if one is discovered in one’s program, it may simply take all of the data of all users. And the easiest method to avoid these types of problems is to use the static analytical process, in which an automated script runs in the background. At the same time, the program is being developed, making it easier for the developer to fix the issue right away rather than later.